New: Become a sponsor via GitHub Sponsors!
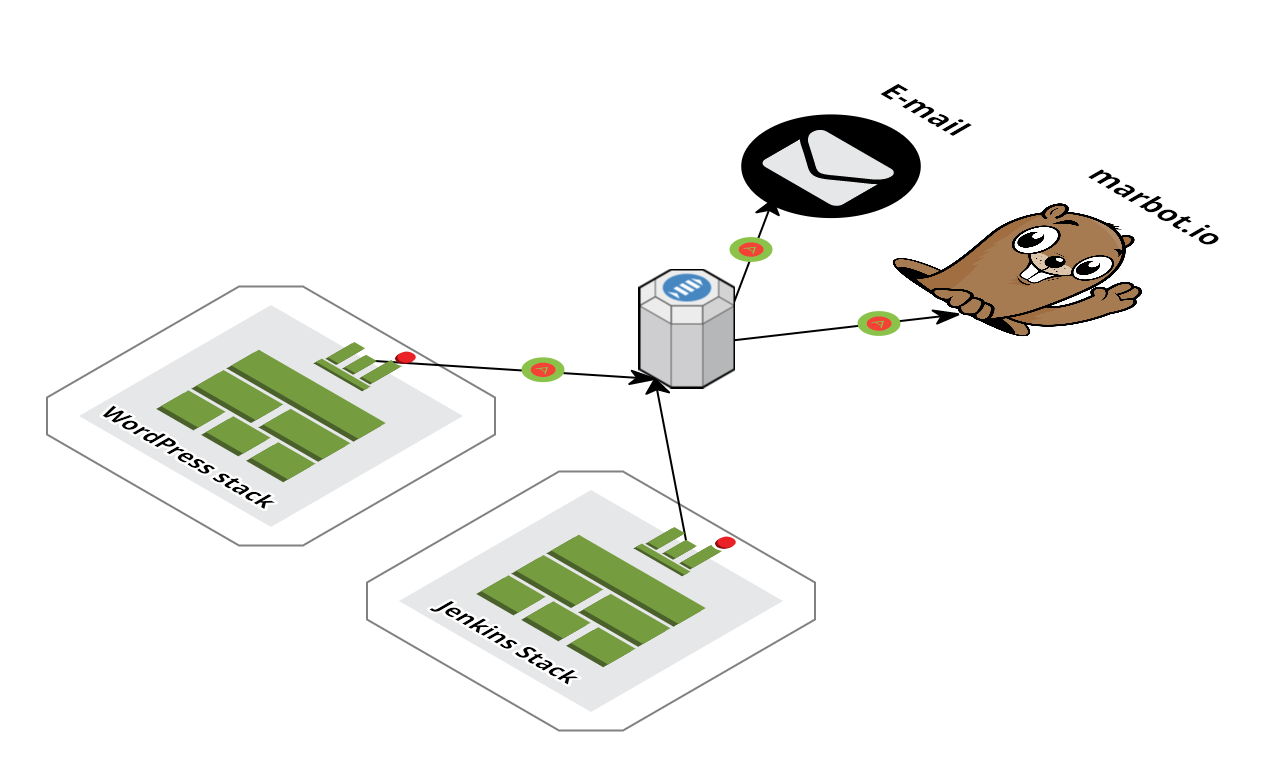
Alert topic
This template describes a SNS topic that can be used by many other templates to receive alerts. You can add one or multiple subscribers to this topic and they will all receive the same alerts. Supported transports are: * Email * HTTP endpoint * HTTPS endpoint (can be used by marbot)
Amazon S3 URL: https://s3-eu-west-1.amazonaws.com/widdix-aws-cf-templates-releases-eu-west-1/stable/operations/alert.yaml
marbot
AWS Monitoring from Slack and Microsoft Teams. Configure monitoring, receive alerts, solve incidents.
marbot sets up CloudWatch Alarms and EventBridge Rules for all parts of your AWS infrastructure. CloudFormation and Terraform are supported.
Your team receives alerts as direct messages or channel messages via Slack. The alert includes relevant details to understand and solve the problem. Use different Slack channels to separate prod from dev alerts. Only get alerted when necessary. To avoid a flood of alarms, marbot groups similar events.
Strong integrations with AWS and 3rd party services: AMI, Auto Scaling, Budget, CloudFormation, CloudWatch Alarms, CloudWatch Events, CodePipeline, DynamoDB, EC2, Elastic Beanstalk, ElastiCache, ELB, EMR, KMS, Lambda, RDS, S3, SES, SNS, Trusted Advisor, X-Ray, Bitbucket, Email, HTTP(S), Jenkins, New Relic, RSS Feed, Sumo Logic, Uptime Robot, ...
marbot escalates an alert to a single team member. Each alert can either be acknowledged, passed on, or closed. Unnoticed alerts are escalated to another team member or the whole crew if needed.
marbot adds Quick Links pointing to the AWS Management Console automatically. marbot attaches runbooks to provide structured procedures to respond to incidents as well.
Each week, marbot rewards team members for closing alerts. The detailed statistics help you to optimize your alert configuration as well.
Installation Guide

- Click Next to proceed with the next step of the wizard.
- Specify a name and all parameters for the stack.
- Click Next to proceed with the next step of the wizard.
- Click Next to skip the Options step of the wizard.
- Check the I acknowledge that this template might cause AWS CloudFormation to create IAM resources. checkbox.
- Click Create to start the creation of the stack.
- Wait until the stack reaches the state CREATE_COMPLETE
Access Logs Anonymizer
IPv4 addresses are anonymized to XXX.YYY.ZZZ.0 and IPv6 addresses to XXXX:YYYY::.
Access logs are stored in S3 buckets (created via state/s3). The following order of creation is recommended:
- Create S3 Bucket stack.
- Create Access Logs Anonymizer stack.
- Update S3 Bucket stack and set the parameter LambdaFunctionArn to the FunctionARN output of the Access Logs Anonymizer stack.
CloudFront
This template describes a Lambda function that can be used to anonymize IP addresses in CloudFront access logs.
Amazon S3 URL: https://s3-eu-west-1.amazonaws.com/widdix-aws-cf-templates-releases-eu-west-1/stable/operations/cloudfront-access-logs-anonymizer.yaml
Installation Guide
- This template depends on our
state/s3.yamltemplate.

- Click Next to proceed with the next step of the wizard.
- Specify a name and all parameters for the stack.
- Click Next to proceed with the next step of the wizard.
- Click Next to skip the Options step of the wizard.
- Check the I acknowledge that this template might cause AWS CloudFormation to create IAM resources. checkbox.
- Click Create to start the creation of the stack.
- Wait until the stack reaches the state CREATE_COMPLETE
- Update S3 Bucket stack and set the parameter LambdaFunctionArn to the FunctionARN output of the Access Logs Anonymizer stack.
Dependencies
state/s3.yaml(required)operations/alert.yaml(recommended)
ALB
This template describes a Lambda function that can be used to anonymize IP addresses in ALB access logs.
Amazon S3 URL: https://s3-eu-west-1.amazonaws.com/widdix-aws-cf-templates-releases-eu-west-1/stable/operations/alb-access-logs-anonymizer.yaml
Installation Guide
- This template depends on our
state/s3.yamltemplate.

- Click Next to proceed with the next step of the wizard.
- Specify a name and all parameters for the stack.
- Click Next to proceed with the next step of the wizard.
- Click Next to skip the Options step of the wizard.
- Check the I acknowledge that this template might cause AWS CloudFormation to create IAM resources. checkbox.
- Click Create to start the creation of the stack.
- Wait until the stack reaches the state CREATE_COMPLETE
- Update S3 Bucket stack and set the parameter LambdaFunctionArn to the FunctionARN output of the Access Logs Anonymizer stack.
Dependencies
state/s3.yaml(required)operations/alert.yaml(recommended)
GitHub OpenID Connect
Allow GitHub Actions to assume IAM Roles in your AWS account without IAM users.
Amazon S3 URL: https://s3-eu-west-1.amazonaws.com/widdix-aws-cf-templates-releases-eu-west-1/stable/operations/github-openid-connect.yaml
Installation Guide

- Click Next to proceed with the next step of the wizard.
- Specify a name and all parameters for the stack.
- Click Next to proceed with the next step of the wizard.
- Click Next to skip the Options step of the wizard.
- Check the I acknowledge that this template might cause AWS CloudFormation to create IAM resources. checkbox.
- Click Create to start the creation of the stack.
- Wait until the stack reaches the state CREATE_COMPLETE
Terraform State
Creates S3 bucket and DynamoDB table used to manage remote Terraform state.
Amazon S3 URL: https://s3-eu-west-1.amazonaws.com/widdix-aws-cf-templates-releases-eu-west-1/stable/operations/terraform-state.yaml
Installation Guide
- This template depends on our
security/kms.yamltemplate.

- Click Next to proceed with the next step of the wizard.
- Specify a name and all parameters for the stack.
- Click Next to proceed with the next step of the wizard.
- Click Next to skip the Options step of the wizard.
- Click Create to start the creation of the stack.
- Wait until the stack reaches the state CREATE_COMPLETE
Be aware that the template creates a bucket policy using a
Denystatement with aNotPrincipalelement when defining theTerraformStateUserARNsandTerraformStateAdminARNsparameters. Therefore, both parameters should include the following inforamtion: account ARN (e.g.,arn:aws:iam::111111111111:root), IAM user (e.g.,arn:aws:iam::111111111111:user/tfuser), IAM role (e.g.,arn:aws:iam::111111111111:role/tfadmin) and assumed-role user (e.g.,arn:aws:sts::111111111111:assumed-role/tfadmin/session). Check out NotPrincipal with Deny to learn more.
Dependencies
security/kms-key.yaml(required)